
Converting Old RAR Archives to Modern Formats: Safety and Benefits
Many organizations and long-time users still rely on RAR4 archives created years ago. These legacy files often contain sensitive project data, legal materials, internal records, or long-term backups. But as software, encryption standards, and corporate workflows evolve, older RAR formats can quietly become liabilities: slower performance, weaker integrity protections, limited metadata, and compatibility issues with modern tools.
This article explains why upgrading old RAR4 archives to modern RAR5 formats can significantly improve security, resilience, and future usability. We also look at how to evaluate risks, preserve integrity, and migrate safely — all without exposing data or relying on risky online tools. Whether you manage corporate archives or personal backups, modernizing legacy RAR files can strengthen long-term access and reduce the danger of opening fragile, outdated containers years from now.
🧭 Navigation
Important
The information provided in this article applies exclusively to RAR / WinRAR archives for which you have full, demonstrable ownership or properly documented authorization. If you are not the rightful owner of the data, do not directly control it, or cannot clearly prove permission to access it, you must stop immediately. Attempting to access, recover, or modify data without explicit authorization may violate criminal law, civil statutes, corporate compliance requirements, and privacy regulations in many jurisdictions. You alone are responsible for ensuring that your actions are lawful and properly permitted before proceeding.
📌 TL;DR — RAR4 vs RAR5 Conversion Explained Simply
RAR4 archives still work, but they lack many modern protections and efficiency improvements introduced in RAR5. If your archives store important or sensitive data, upgrading helps protect long-term access. Older archives may also suffer from weaker metadata, less resilient recovery structures, and limited header protection — which can create bottlenecks years later when your organization needs to access legacy information safely.
A safe migration plan involves: (1) verifying that the archive opens and is intact, (2) confirming that your organization legitimately owns the data, (3) extracting contents in a controlled environment, (4) re-archiving them using modern RAR5 settings, and (5) validating final integrity. This provides stronger encryption, improved recovery records, better format transparency, and reduced future risk. Conversion is not urgent for every scenario, but for long-term storage, regulatory needs, or corporate workflows, upgrading provides meaningful and durable security benefits.
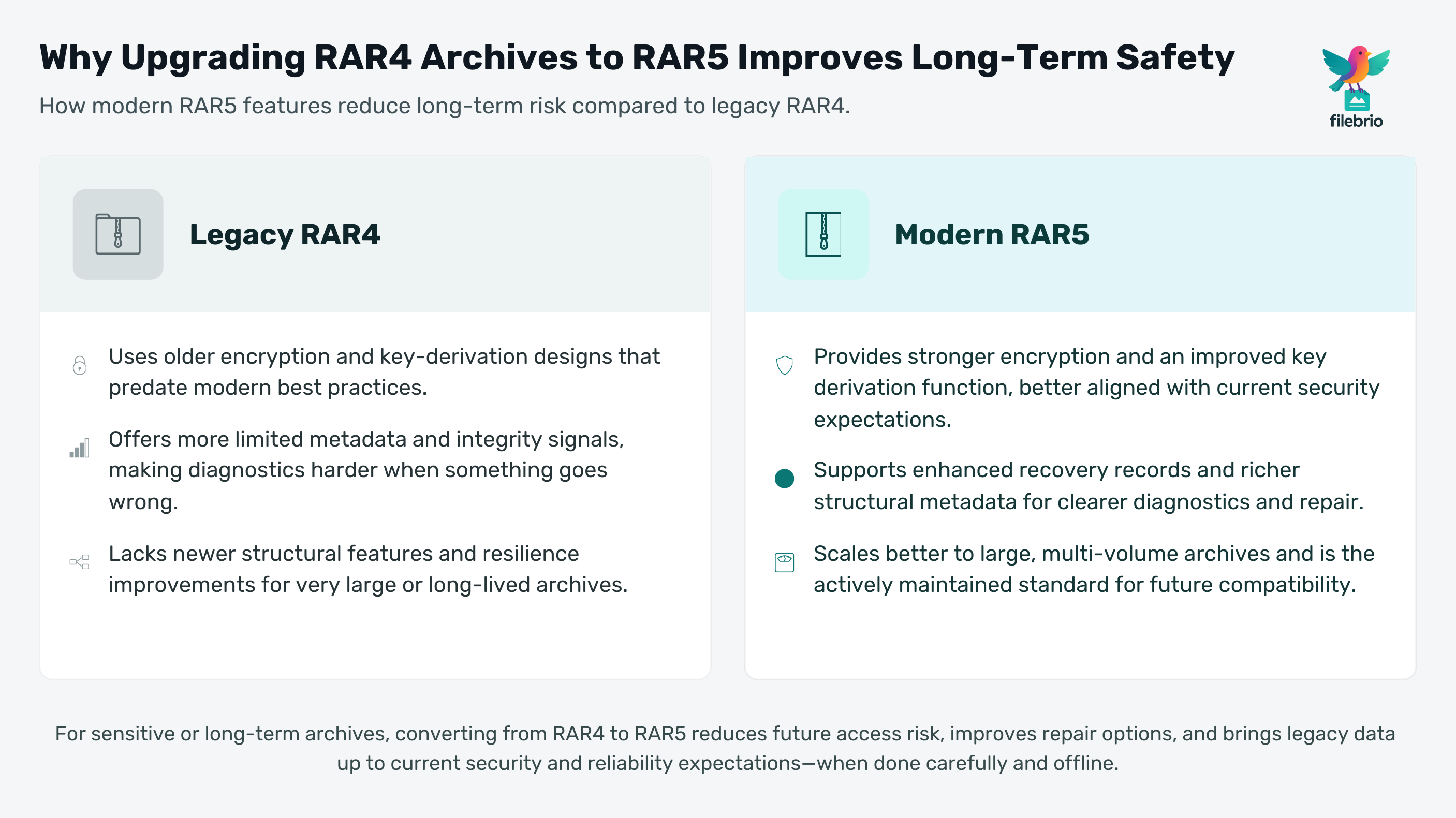
🚀 Why Modernizing Old RAR Archives Matters
Legacy RAR4 archives remain widespread because they were the default for many years. Millions of older project backups, internal documents, and personal archives were created using this format. But several changes in the security landscape have made RAR4 less ideal for long-term storage:
- Encryption strength: RAR4 uses older cryptographic design choices that predate current best practices.
- Integrity limitations: metadata and header behavior can limit diagnostics when something goes wrong.
- Compatibility forward, not backward: modern tools support RAR4, but older tools may mis-handle RAR5, making it harder to maintain mixed environments.
- No structural improvements: RAR4 lacks some resilience features that protect against partial corruption.
These aren’t “immediate threats,” but they become significant over years or decades. Long-term corporate archives especially benefit from migrating to modern formats to reduce recovery risk and ensure future teams can still access data without surprises.
Many organizations first assess whether the archive is even technically viable before planning conversion; comprehensive approaches like how to verify recoverability of your locked RAR file ↗️ help ensure that a legacy archive is healthy enough to undergo conversion safely.
🔐 Key Security and Reliability Benefits of RAR5
RAR5 is not just a “newer version” — it brings structural improvements that significantly impact security, diagnostics, and long-term reliability. The main benefits include:
1. Stronger Encryption & KDF Improvements
RAR5 introduced a modernized key derivation function, improving resistance to unauthorized attempts and aligning more closely with contemporary security expectations. For corporate or sensitive archives, this aligns with broader guidance on why the RAR5 KDF matters for security ↗️.
2. Enhanced Recovery Records
One of the most important upgrades is more robust recovery records. These can make the difference between a corrupted archive being salvageable or permanently unreadable. For administrators, it pairs naturally with knowledge of how recovery records and .rev volumes protect data ↗️.
3. Modern Format Transparency
RAR5 metadata and structural improvements help tools understand where corruption lies and what can be recovered. These structural signals greatly improve diagnostics during incidents.
4. Scalable Performance for Large Archives
RAR5 handles large files and multi-core systems more efficiently, improving both compression behavior and extraction performance — important for enterprise workflows or large, multi-volume archives.
5. Better Header Behavior and Protection
RAR5 archives can include encrypted headers, improving privacy and preventing metadata leakage. For context, organizations concerned with visibility limitations often review how header encryption affects content discovery ↗️ before planning conversions.
6. Prospective Longevity
RAR5 is the actively maintained modern standard. RAR4 is now legacy. Converting helps ensure continuity even as tools evolve.
🛠️ All-in-One Workspace for Safe RAR4 → RAR5 Conversion
For many teams, the biggest challenge is not the conversion itself but ensuring that it is done safely without exposing sensitive data, corrupting fragile archives, or mixing workflows across multiple semi-trusted utilities.
FileBrio RAR Master helps resolve these gaps by acting as a focused, offline-safe environment for handling your own RAR archives: extraction, inspection, diagnostics, and re-archiving included. This is especially valuable for legacy archives whose contents must remain private and whose integrity you cannot risk during conversion.
| Conversion Need | Corporate Risk | How a Unified Workspace Helps |
|---|---|---|
| Open old RAR4 archives safely | Legacy formats may be fragile or corrupted | Controlled offline environment reduces risk |
| Repackage to RAR5 | Extraction and re-archiving must not leak data | No cloud upload; operations stay local |
| Verify integrity and structure | Silent corruption can break archives during migration | Diagnostic features help identify issues early |
Teams managing long-term archives or regulated data appreciate having a predictable, compliance-friendly workspace with consistent behaviors rather than improvising with random utilities that may not follow internal rules.
________________________
FileBrio RAR Master — part of the FileBrio Office Suite — is a privacy-first, offline Windows toolkit for diagnosing and safely regaining access to your own password-protected RAR / WinRAR archives.
- Local processing only — nothing leaves your PC.
- Smart diagnostics to separate password issues from corruption.
- Owner-verified recovery workflows designed strictly for legitimate use.
Reminder: FileBrio RAR Master may be used only with archives you own or are explicitly authorized to access. It performs all analysis and recovery operations locally on your device, without uploading data anywhere.
________________________
🩺 Diagnostic Steps Before Converting Legacy RAR Files
Before converting a legacy RAR4 archive, validate its health. Converting a damaged or partially corrupted archive may “lock in” the damage or make issues harder to detect later. A structured diagnostic phase helps prevent this.
Typical steps include:
- Check file integrity using safe metadata inspection to determine whether the archive is complete.
- Verify ownership to ensure you have legitimate rights to work with the archive — guidance is available on how to verify ownership before accessing your RAR file ↗️.
- Inspect metadata for structure irregularities.
- Identify corruption or missing segments before extraction.
- Review long-term feasibility following methods similar to how to assess safe access paths for your locked RAR file ↗️.
If any corruption appears, evaluate whether recovery blocks or .rev volumes exist. They may help restore missing segments before migration. When working with multi-volume archives, consult insights in how passwords behave across multi-volume archives ↗️.

🧱 Ensuring Data Integrity and Avoiding Silent Corruption
Silent corruption is one of the greatest risks during legacy file conversion. RAR4 archives may contain fragile segments that extract correctly only under specific conditions. To avoid integrity loss:
- Extract to an isolated environment so corruption does not propagate into production backups.
- Verify checksums on extracted files when possible.
- Inspect the archive’s internal structure using safe, non-extractive analysis methods like how to inspect the internal layout of your RAR file safely ↗️.
- Confirm metadata consistency using guidance from how to read RAR metadata to understand what went wrong ↗️.
Once extraction is validated, create a new RAR5 archive using your organization’s security policies, password standards, and encryption settings. Tools that support enhanced metadata and long-term access strategies are ideal, particularly when following broader guidance on how to reinforce protection while keeping future access open ↗️.
🛡️ Secure Offline Tools and Workflows for Safe Conversion
It is essential that conversion workflows stay offline. Uploading old RAR4 archives to online “conversion” or “repair” sites introduces privacy, compliance, and security risks. The safest method is entirely local: extract locally, re-archive locally, store locally, and validate locally.
Corporate workflows typically include:
- Trusted endpoints: conversion occurs on secured machines.
- Documented approval: ownership and authorization are confirmed.
- Offline tooling: metadata, passwords, and file contents stay inside corporate infrastructure.
- Integrity verification: final archives are checked before distribution or archival.
Tools like RAR password recovery ↗️ features can be integrated into your workflow when dealing with legacy archives whose passwords have been lost but which must be recovered before conversion. Guidance on handling abandoned archives can be found in how to evaluate your situation after losing a RAR password ↗️.
Once recovered and repackaged, the organization gains a modern RAR5 archive that meets current security guidelines and reduces future risk — without exposing data during conversion.
________________________
FileBrio RAR Master — a secure, offline Windows toolkit for regaining access to your own password-protected RAR / WinRAR archives while keeping all data strictly on your device.
- Offline-only processing — never uploads your archives.
- Smart issue detection — password vs corruption.
- Fast recovery workflow optimized for legitimate ownership.
⬇️ Download FileBrio RAR Master
Reminder: FileBrio RAR Master is intended only for archives you own or are explicitly authorized to access. All operations run locally on your PC.
________________________
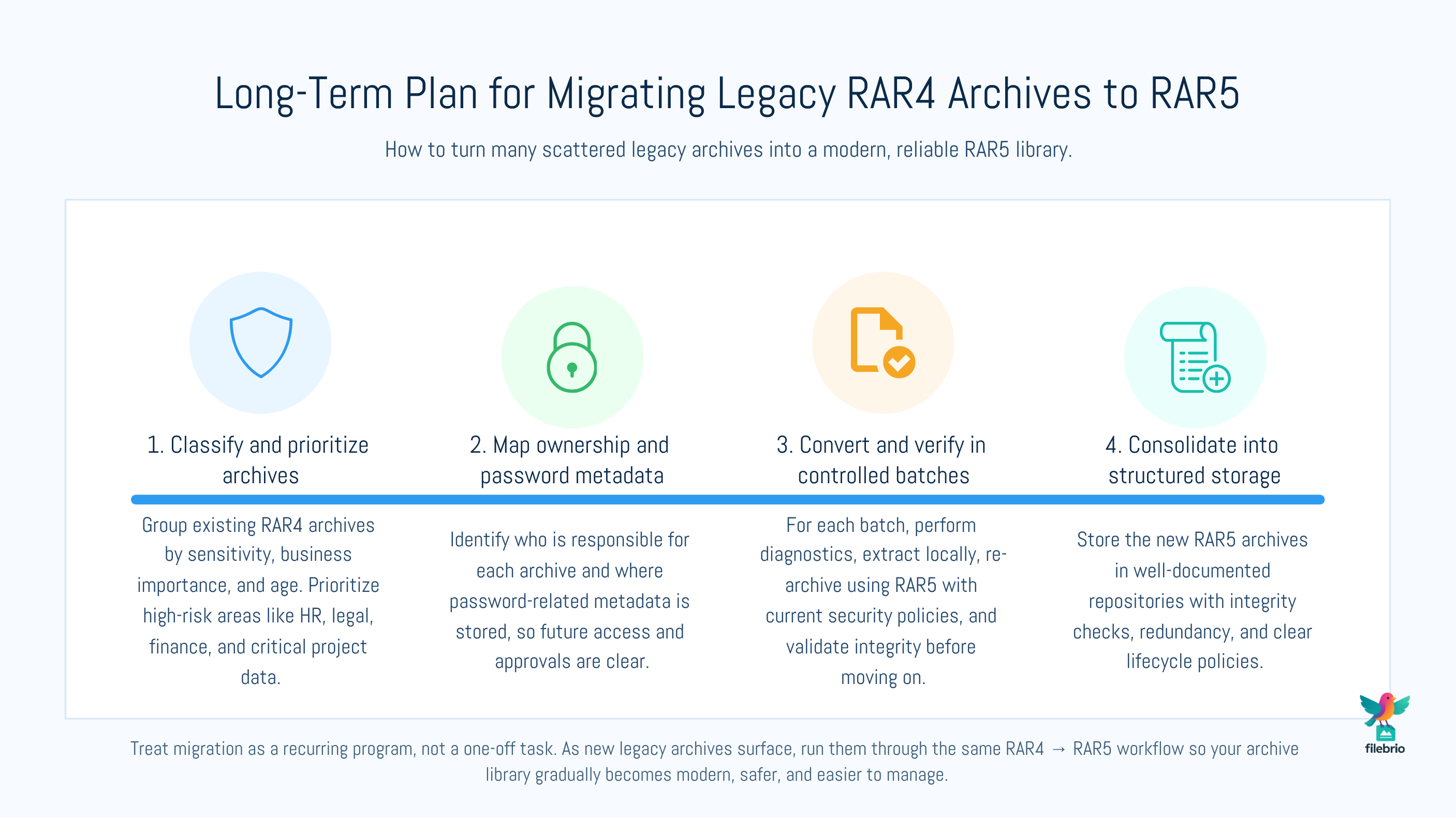
📦 Planning Long-Term Migration and Archive Consolidation
Converting one archive is straightforward. Converting hundreds or thousands — common in enterprise environments — requires planning.
Key elements of a safe migration strategy include:
- Classifying legacy archives by sensitivity level and business importance.
- Identifying long-term custodians following guidance such as how teams can preserve long-term access to encrypted RAR files ↗️.
- Mapping password metadata and ownership using frameworks similar to how teams organize RAR password metadata safely ↗️.
- Migrating high-risk archives first (HR, legal, financial, product IP).
- Consolidating scattered archives into structured storage with documented workflows.
Once a modern RAR5 archive is created, store it in a controlled repository with integrity checks, redundant copies, and well-documented ownership. This ensures future longevity and reduces the likelihood of problems arising during audits or reaccess.
Properly executed, RAR4 → RAR5 migration prevents future operational surprises and strengthens the organization’s overall data resiliency.
⚖️ Legal Reminder and Responsible Use
This article is provided for general informational and educational purposes only. Any examples, scenarios, or references to password recovery, archive security, or related tools (including FileBrio RAR Master or similar software) are intended solely to help you better understand how to protect and manage your own data.
You may only apply any techniques, workflows, or tools described here to files and archives that you fully own or are explicitly and verifiably authorized to access. Attempting to bypass, remove, or recover passwords for third-party data without clear permission may violate criminal law, civil law, or internal company policies in your jurisdiction.
Nothing in this article constitutes legal advice. Laws and regulations differ between countries and organizations, and you are solely responsible for ensuring that your actions comply with all applicable legislation, contracts, and internal policies. If you are unsure whether a particular action is lawful or permitted, consult a qualified legal professional before proceeding.
🔗 See Also: Related RAR Security and Migration Guides
- Understanding Multi-Volume RAR Archives: Password Behavior and Repair Options ↗️
- How to Avoid Losing Access to Decade-Old RAR Archives ↗️
- Why RAR5 Is More Secure — and What That Means for File Access ↗️
- RAR Encryption Explained: How RAR4 and RAR5 Protect Your Data ↗️
- How to Safely Evaluate RAR Protection Using Dummy Archives ↗️
- How to Document Ownership of Sensitive Encrypted Archives ↗️
- How to Strengthen RAR Archive Security While Preserving Future Access ↗️